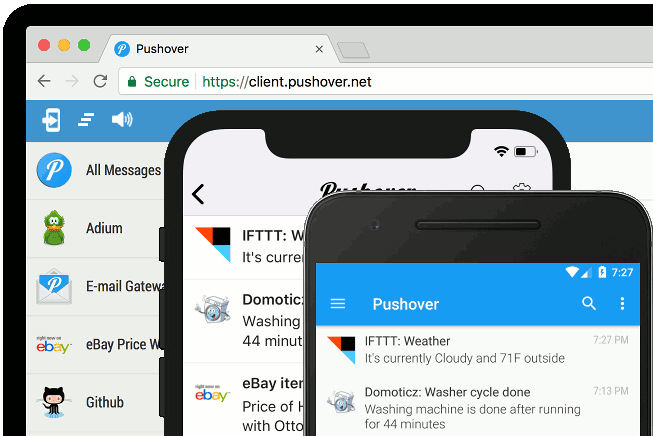
BASH Pushover Notifications
A few days ago, I started a process that involves very heavy file processing operations that take anywhere from 10 minutes on the low side to 30 minutes on the high side. Wanting to be as efficient as possible and not let the computer sit idle for any meaningful length of time, and since the …